The Ultimate Strategy to Maximize Your Splunk Security Posture
Stop adding random detections. Start with this proven framework.
Hey Splunkers,
Most security teams are doing detection engineering completely backwards.
They add new detection rules sporadically, often driven by the latest security incident, a concerning penetration test finding, or simply because a SOC analyst thinks it might be valuable. While each of these triggers has merit, this ad-hoc approach creates serious blind spots. Making matters worse, these teams typically lack visibility into their existing detection coverage.
I once fell into this trap myself, until I crafted a framework that revolutionized the way I advise the teams I support on shaping their Splunk security monitoring strategies.
In today's newsletter, I'm sharing my battle-tested 6-step framework for building a strategic security monitoring program in Splunk that actually works. You'll learn:
How to map your current security coverage (and why most teams get this completely wrong)
A systematic approach to finding and filling critical detection gaps
The right way to leverage Splunk's pre-built content to accelerate your security maturity
And much more. Let's dig into why the standard approach to security monitoring is fundamentally broken - and how to fix it.
The Challenge: Reactive Security in an Active Threat Landscape
Most security teams that I’ve observed, despite their best intentions, fall into a reactive pattern of detection implementation.
As a Splunk security consultant who’s supported numerous organizations over the past 4 years, I've seen the same pattern emerge time and again: teams frantically building new detections based on the latest breach news or pen test findings, while having zero insight into their actual security coverage. The worst part? These same teams are sitting on a goldmine of analytical dashboards and pre-built security content that could solve their problems - they just don't know how to use it effectively.
Ask a security leader about their coverage across the MITRE ATT&CK framework, and you'll often get a vague response or an admission that they're not sure.
Without this fundamental understanding, how can teams make strategic decisions about where to focus their detection engineering efforts?
A reactive approach leads to
Inconsistent detection
Redundancy
Gaps in monitoring
Inefficient use of time
Waste of resources
And ultimately, an ineffective Splunk security monitoring strategy.
However, by adopting a mindful and proactive strategy, leveraging Splunk's pre-built security content, and adopting a continuous feedback loop of improvement, organizations can not only gain complete visibility into their monitoring capabilities, their CISO’s can sleep soundly at night knowing that their security posture is sound.
The foundation of this approach is a comprehensive assessment framework that provides a clear understanding of the current state before charting the path forward.
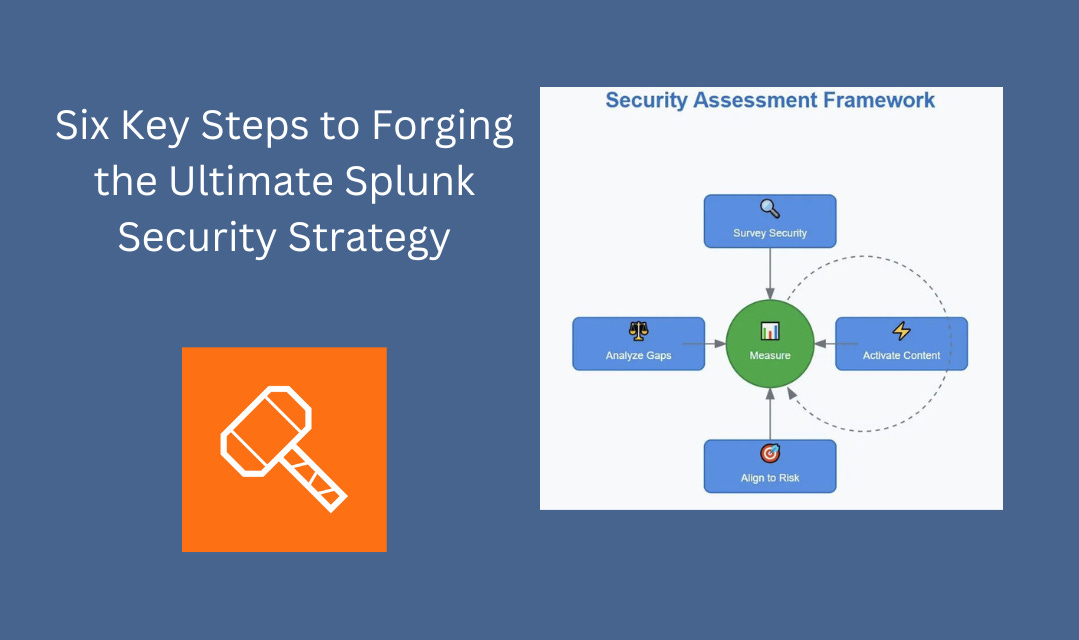
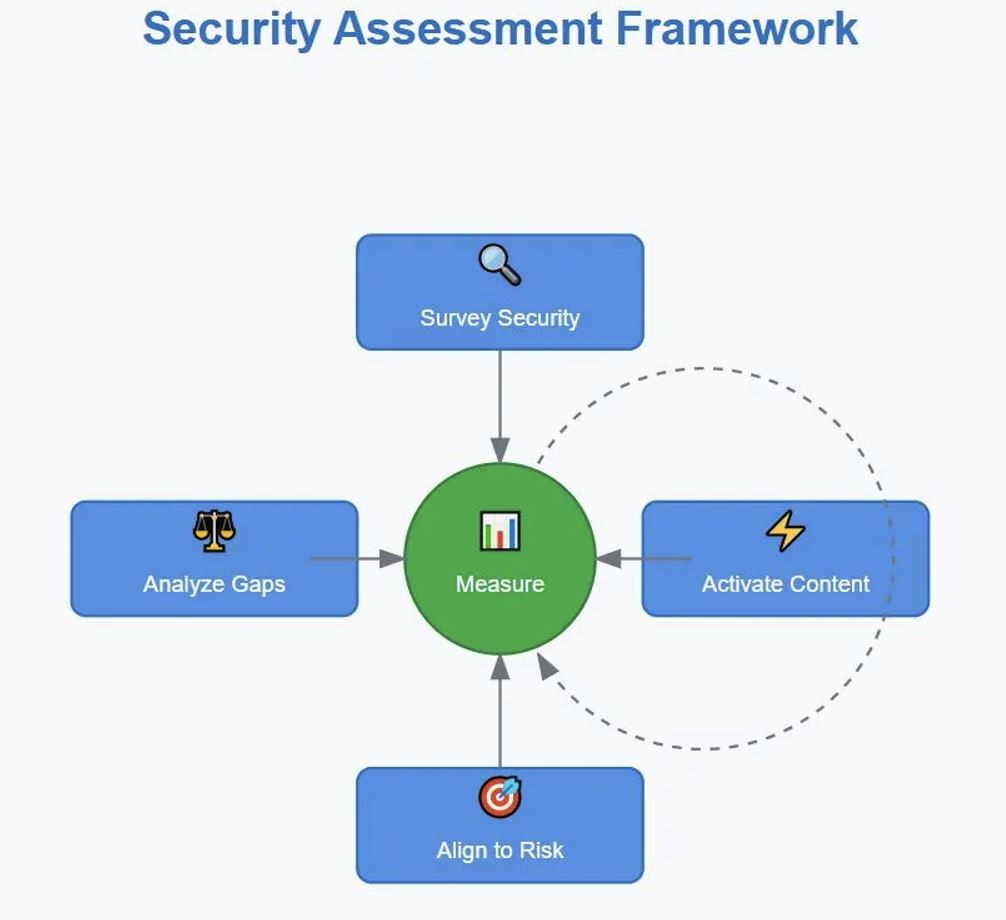
The 6-Step Security Assessment Framework
Step 1: Identify Your Security Monitoring Strategy
Your organization could have all of the advanced Splunk security tools (SIEM, SOAR, UBA, Attack Analyzer, and more), but if it doesn’t have a sound security monitoring strategy or plan for implementing them and maximizing their potential, they aren’t going to be all that effective.
Believe it or not, I’ve worked with organizations that when asked what their security strategy is, they couldn’t answer it.
And this wasn’t Walmart, this was a large government agency.. but I digress.
Ask yourself this - does your organization have a robust security monitoring strategy in place?
If it does, then that’s a good sign. But you’ll also need to consider this - has it been reviewed or revised in the last five years? If not, it might be time to discard it and invest some effort here to identify the critical areas that need monitoring within your organization. Such an assessment lays the groundwork for developing robust security posture criteria.
It's perfectly acceptable for your organization to start by covering the essential security bases, especially if there are no specific attack vectors of particular concern. However, what if you are part of an enterprise with significant volumes of valuable intellectual property, technology, or trade secrets? The risk of an advanced threat infiltrating your networks and exfiltrating sensitive data could be catastrophic. In such cases, it is crucial to devote additional attention to threat vectors such as data exfiltration.
Furthermore, consider the cybersecurity models or frameworks your security team utilizes. Here are a few examples:
They are all solid frameworks, but I personally recommend the MITRE ATT&CK framework.
While all of the above models are helpful in their own right, MITRE’s framework provides for the most helpful, actionable, and robust framework for mapping actual adversary threats via tactics, techniques, and procedures to security content in Splunk. There are a number of MITRE ATT&CK based apps and pre-built dashboards that can provide direct heatmap overlay’s to your existing and/or enabled security content in Splunk. Furthermore, Splunk has gone through great lengths in mapping their security alerts to MITRE TTPs.
This not only saves you the trouble of having to do this yourself, it provides for a foundational step for analyzing your overall security posture.
Bottom Line: A security monitoring strategy isn't a set-it-and-forget-it exercise. MITRE ATT&CK provides the most practical framework for modern security operations, offering clear mappings to Splunk's security content and enabling rapid gap analysis. Whether you're starting fresh or revamping existing coverage, focus on building a strategy that evolves with your threat landscape. The frameworks and tools exist - your job is to implement them effectively for your organization's specific needs.
Remember: Perfect security doesn't exist, but purposeful security monitoring does. Start with identifying what matters most to your business and build from there.
Step 2: Survey Your Security Landscape
Objective: Establish a comprehensive baseline of your organization's current security stack and logging coverage to identify strengths and pinpoint weaknesses.
Understanding your starting point is crucial for advancing toward a robust security posture. What security sources do you have in your environment? What logs are you collecting? EDR, Firewall, IDS, DLP, and others typically come to mind first and should all be forwarding their data to Splunk. But what about SaaS logs such as Google Workspace, or AWS security events, or Slack audit logs?
These are critical to monitor as well.
Without a clear picture of your current security stack and logging state, any security enhancements may be misaligned with your organization’s actual needs.
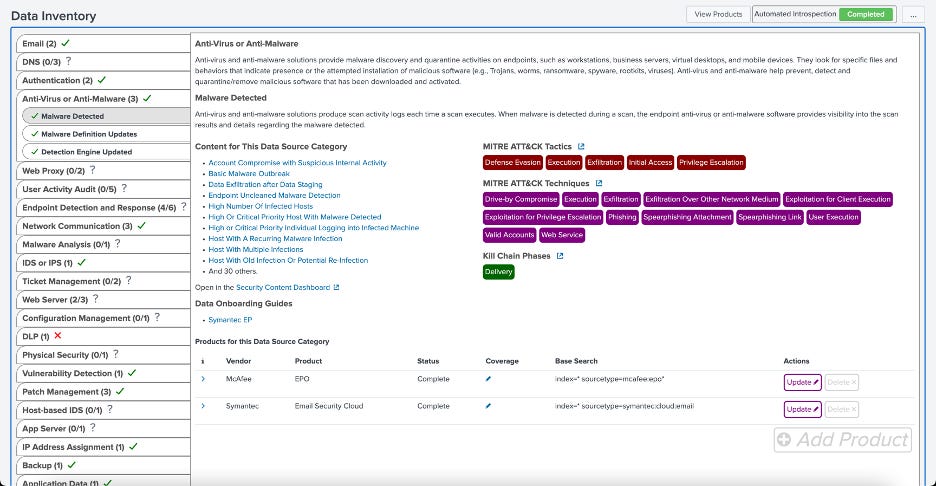
Splunk Implementation Tip: Use the Splunk Security Essentials (SSE) Data Inventory capability to automatically evaluate your security data sources. This tool not only identifies which data sources that your Splunk environment is logging, but it can also map them to specific security use cases and MITRE ATT&CK techniques. By leveraging this tool, you can see where your monitoring strategy aligns with industry standards and where it falls short, providing a clear roadmap for enhancement.
In this step, the goal is not just to understand what data sources you have, but to critically assess its effectiveness and prepare for strategic improvements.
This detailed assessment ensures that your security monitoring strategy is not only aligned with current threats but also robust enough to adapt to emerging challenges.
Bottom Line: Your security monitoring strategy is only as good as the data feeding it. Start with a thorough inventory using Splunk Security Essentials' Data Inventory feature - it's like running diagnostics before upgrading your car's engine. You might discover you're missing critical logs (blind spots) or collecting data you never use (wasted resources). Security tools are expensive - make sure you're getting value from each one before adding more to the stack. Remember: you can't detect what you can't see, and you can't respond to what you can't detect.
Pro Tip: Keep your data source inventory document current. When the next security incident happens, you'll want to know exactly what logs you have available for investigation.
Step 3: Analyze Gaps and Overlaps
Objective: Identify critical security coverage gaps and resource-draining redundancies
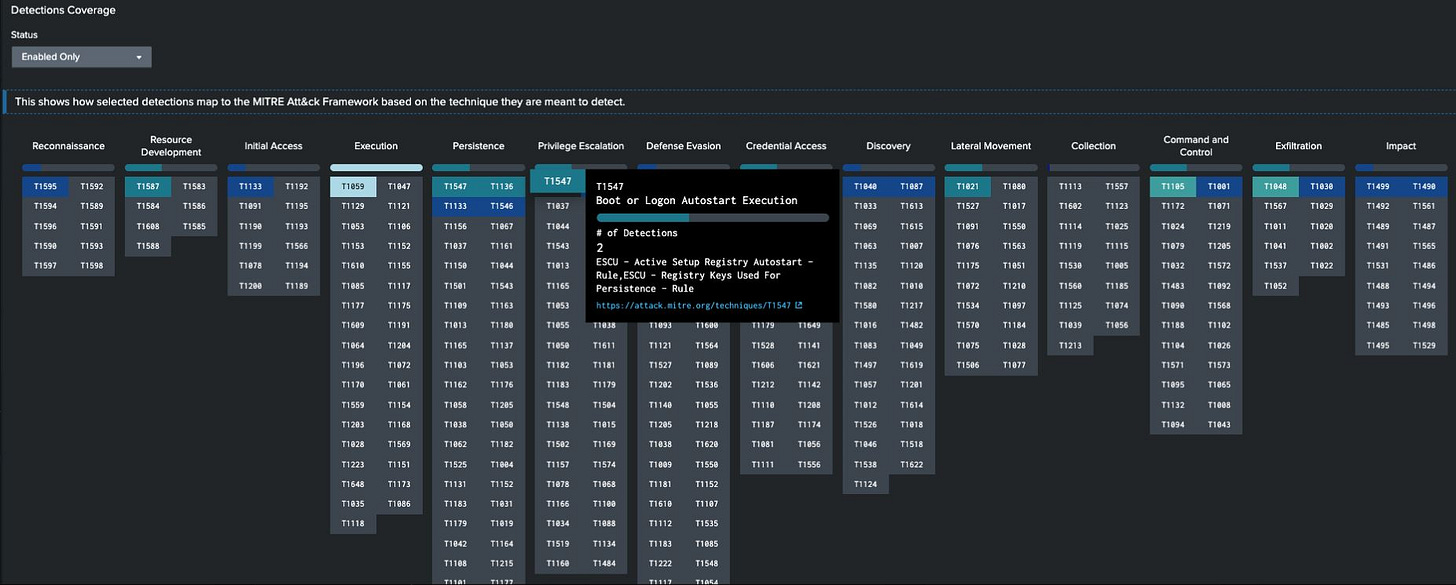
When evaluating your security content coverage, leveraging MITRE ATT&CK heat mapping capabilities within Splunk is essential for identifying blind spots in your detection strategy. Here are three powerful Splunkbase applications that can be deployed on your search heads to gain immediate visibility into your MITRE TTP coverage:
This is the go-to starting point for most organizations due to its out-of-the-box content and ease of use.
The app not only provides MITRE mapping capabilities but also includes ready-to-use security content, making it invaluable for teams looking to quickly establish a baseline security posture. The built-in guidance and implementation steps for each security use case make it particularly effective for teams with varying levels of Splunk expertise.
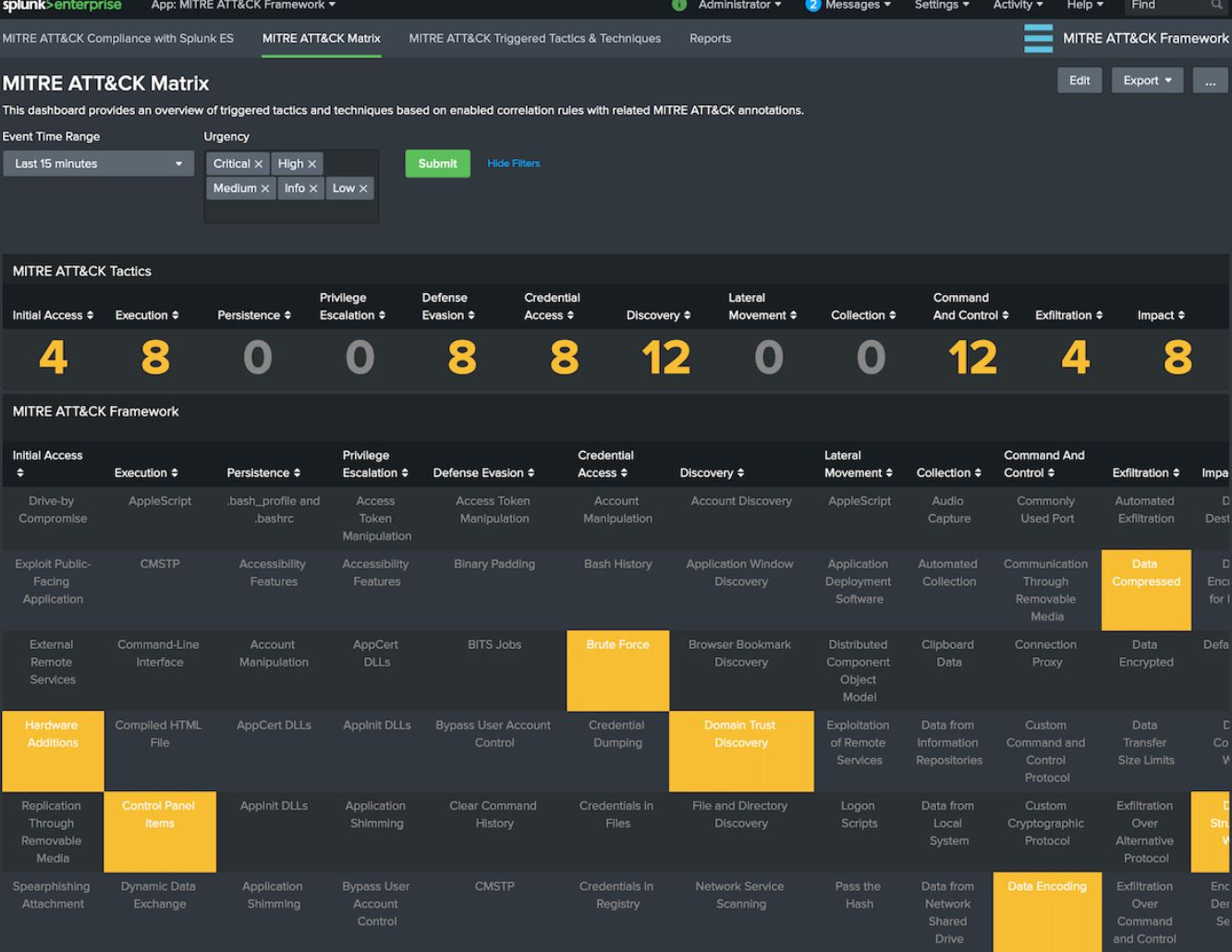
Provides an intuitive heat map overlay of your existing security searches and alerts
Maps current detection content directly to MITRE ATT&CK techniques
Ideal for teams beginning their MITRE mapping journey due to its straightforward interface
This app represents one of the most comprehensive deep-dives into MITRE ATT&CK mapping available in the Splunk ecosystem. Its strength lies in its ability to provide granular visibility into technique coverage and the relationships between different TTPs. Where SSE excels at showing what a heatmap of what content is available and enabled, this app excels at showing a MITRE heat map of what alerts have triggered in your environment.
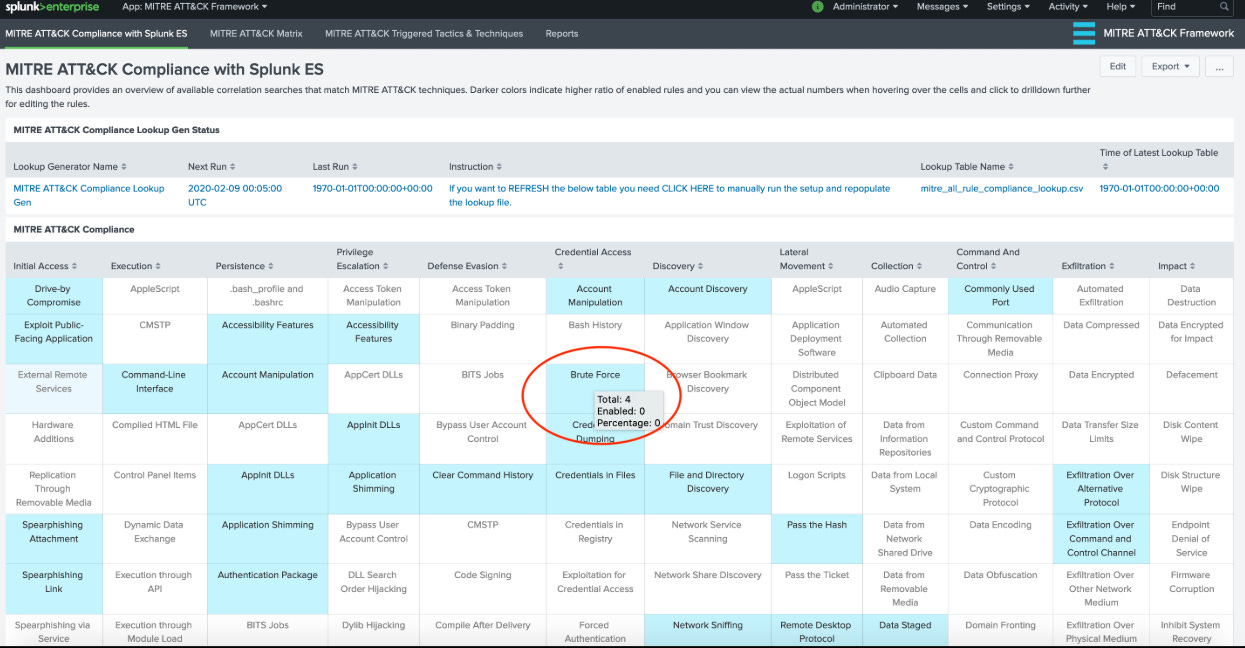
SA-DetectionInsights (for Enterprise Security customers)
This is the premium option for mature security operations centers that have already invested in Splunk Enterprise Security. The app's integration with your ES detections provides a comprehensive picture across all of your Splunk alerts.
The MITRE ATT&CK Details tab shows you details around your detections and how they map to the MITRE ATT&CK security framework. You can optionally view different versions of the MITRE matrices (Enterprise, ICS, Mobile, Containers, etc.). You'll be presented with:
Your current detection coverage
The additional coverage available but currently not in use
Triggered detections coverage
How your posture has evolved vs. MITRE based on changes to your Security Detections over time
By leveraging these applications, security teams can transform abstract MITRE mappings into actionable insights, such as massive gaps in your alerting, enabling targeted development of new detection content where it matters most.
Step 4: Align Security Monitoring to Your Risk Profile
Objective: Prioritize detection engineering efforts based on business impact and risk to critical assets.
While this step deserves its own comprehensive guide, we'll focus on the essential elements that drive immediate value. The foundation lies in properly implemented asset and identity frameworks, ideally coupled with risk-based alerting capabilities through Splunk Enterprise Security. These types of capabilities usually require the support of Splunk professional services, but if you have a high speed Splunk engineer, they may be able to do the job.
Ultimately, you’ll need to start with what matters: mapping your MITRE coverage against business impact. If privileged access management drives your compliance requirements, prioritize detecting techniques like T1078 (Valid Accounts) and T1548 (Abuse Elevation Control Mechanism). Healthcare organizations might focus on EHR system access, while manufacturing prioritizes OT system integrity.
Next, transform technical findings into business context. Instead of reporting "missing T1505.003 coverage," highlight the "web shell blind spot that could expose customer data." This translation drives stakeholder action and budget allocation.
Essential Focus Areas:
Critical assets first - customize risk scoring based on both asset value and attack technique
Industry threats matter - healthcare priorities differ fundamentally from retail concerns
Compliance drives priorities - map detection thresholds to regulatory requirements
Bottom Line: Risk-Based Alerting (RBA) typically reduces analyst workload by 30-40% or more. Organizations without Enterprise Security should implement custom severity calculations in correlation searches while building the business case for RBA. Focus your detection strategy where business impact meets threat reality - that's what drives results.
Take the time to collaborate across teams on this step. Your security monitoring strategy is only as effective as your understanding of what matters to the business.
Step 5: Strategic Content Activation
Objective: Build a detection arsenal that catches threats without drowning your analysts in alerts.
Look, we've all been there - enabling every detection rule that looks promising, then watching the alerts pile up like spam in your inbox. Let's build something that actually works.
Start with the building blocks. Splunk Security Essentials hands you pre-built content that's already battle-tested. Think of it like a starter home - it gets you living there quickly, and you can renovate later. Focus on those high-priority MITRE techniques you identified in your gap analysis.
Ready to upgrade? That's where ESCU content comes in. But here's the trick - treat each analytic like a blueprint, not a finished product. An example of this could look like a manufacturing client adapting an ESCU process manipulation detection by adjusting the baseline to match their 24/7 operation patterns, and suddenly, their false positives drop by 80%.
Your Testing Toolkit:
Run detections against known-good traffic - if it alerts on everything, it clearly needs tuning.
Measure the performance hit - a detection that takes 2 hours to run probably needs to be optimized.
Define when to tune or retire rules - zombie detections help no one and chew up Splunk resources unnecessarily.
Implementation Path:
Deploy Security Essentials content for quick wins.
Integrate and customize ESCU detections to your environment, and use Analytic Stories for comprehensive threat coverage.
Test against real traffic before going live.
Document your tuning decisions - you'll forget why you made them otherwise.
Bottom Line: Building effective detection content is like cooking - start with proven recipes (Security Essentials, ESCU), adjust the seasoning (tune the rules), then create your own dishes (custom content), once you know what works. Your SOC team will actually respond to alerts instead of drowning in noise.
Keep it practical. Keep it focused. And please, document your work - the next person to tune these detections might be you in six months.
Step 6: Continuous Measurement and Refinement
Objective: Transform security metrics into actionable intelligence that drives continuous improvement.
Let's face it - metrics without context are just numbers on a screen. Building dashboards is easy. Building dashboards that drive actual improvements? That's where the real work happens.
Start with the metrics that matter. Sure, you can track your MITRE technique coverage percentage, but what about the quality of those detections? One well-tuned detection beats ten noisy ones every time. From my observations, the top 20% most effective detections catch 80% of their actual incidents. The Pareto Principle at play, even in Splunk
Your Measurement Arsenal:
Detection Quality: Track true positive rates alongside coverage metrics
Analyst Impact: Monitor alert-to-incident ratios and MTTR by alert type
Business Value: Map detection effectiveness to risk reduction
Here's your optimization roadmap:
Build baselines for each key metric - you can't improve what you don't measure.
Set realistic improvement targets - 100% coverage sounds great but is difficult in practice.
Review and tune underperforming detections monthly.
Kill or tune detections with high false positive rates - they're burning analyst time.
Tool Tip: Enterprise Security's (ES) built-in dashboards turn metrics into visual stories. The Risk Analysis framework adds context by connecting detections to business impact. No ES? Create custom dashboards focusing on actionable metrics.
Bottom Line: Effective security monitoring is a journey, not a destination. Measure what matters, act on the data, and keep refining. Your SOC is either getting better or getting worse - there's no standing still.
Remember: Numbers tell you where you are. Trends tell you where you're going. Focus on the trends that drive improvement.
Implementation Tips and Troubleshooting
Objective: Transform theory into practice without stepping on the usual landmines.
Let's get real about implementation - even the best security strategy can fall apart in execution. This framework I’ve laid out in this newsletter is intended to be a guide, not a strict plan that must be followed to a T. Think of implementing this framework like building a house. You don't start with the roof, and you definitely don't build every room at once. Begin with the foundation, and build up systematically.
The four fatal flaws:
Content Overload: Enabling every detection is like hiring every job applicant - recipe for chaos.
Skipping Dev Testing: That correlation search looks great until it creates 849 alerts in the last 60 minutes.
Flying Blind on Baselines: You can't spot abnormal without knowing normal.
Missing Context: Quality data beats quantity every time.
Your 30-Day Action Plan:
Hold that security workshop - get stakeholders aligned or fail together.
Use pre-built security content and analytics - let it guide your initial decisions.
Map your content rollout to risk priorities - highest risk first.
Build simple dashboards tracking core metrics - complexity comes later.
Schedule monthly content reviews - what worked, what didn't, what's next.
Bottom Line: Success isn't implementing everything - it's implementing the right things right. Start with your critical use cases, test thoroughly, and scale based on results. Your SOC team will thank you for the focused approach.
Questions about implementing this framework in your environment?
Leave a comment below – I'd love to help you get started.
Splunk Security Consultant at NASA
Author of Get Started in Cybersecurity newsletter
Cofounder LinkWell Nodes
Helping security professionals harness the full power of Splunk with step-by-step guidance, security-driven insights, and cutting edge threat hunting techniques.
Tell me what you thought of today's edition of The Splunk Security Forge.
Good?
Ok?
Bad? Hit reply and let me know why.
PS... If you're enjoying The Splunk Security Forge, will you take a few seconds and forward this edition to a friend? It goes a long way in helping me grow the newsletter (and providing security professionals with the Splunk tools and information they need to succeed).
Disclaimer: This newsletter is an independent publication and is not affiliated with, endorsed by, or sponsored by Splunk. All opinions and insights are those of the author.